
On April 9, 2007, the Department of Homeland Security issued the Chemical Facility Anti-Terrorism Standards Regulation Interim Final Rule (CFATS). This regulation was a result of the Department of Homeland Security (DHS) Appropriations Act of 2007, which provided DHS the authority to regulate chemical facility security throughout the country.
CFATS is intended to establish a baseline level of security for facilities considered to pose high risk to the general population in the event of a terrorist attack. It defines security requirements for facilities that use, manufacture, store or handle specific quantities of approximately 323 chemicals that DHS has identified as being extremely dangerous. These chemicals are called “chemicals of interest” (COI) and are listed in Appendix A of the regulation. DHS has conducted a nationwide survey of facilities using these chemicals of interest, resulting in the designation of nearly 7,000 of them as “high risk.” These facilities are subject to the provisions of CFATS.

Figure 1. Tiers
The CFATS Process
The CFATS process is divided into four stages.Step One: Top Screen
The purpose of the Top Screen is to evaluate all facilities housing quantities of potentially hazardous chemicals to develop a ranking on their relative risk. All facilities that used, manufactured, stored or handled any of the roughly 323 chemicals of interest in quantities above DHS-defined threshold limits were required to submit a CFATS “Top Screen” by January 22, 2008. The top screen gathered information on the type and quantity of chemicals used, stored, manufactured or handled by the facility. If the facility did not have these chemicals above the threshold, they were not subject to CFATS.
As a result of the top screen, facilities were divided into four different tiers of risk, based on the potential consequences that could result from a terrorist attack. DHS informed all facilities that submitted a top screen of their initial tier ranking, or confirmed that the facility was not subject to CFATS at that time. The tier letters identified specific chemicals of interest and specific security concerns for each tiered facility. Of the estimated 32,000 facilities that submitted top screens, approximately 7,000 were initially subject to CFATS (see Figure 1).
Step Two: Security Vulnerability Assessment (SVA)
If the top screen divided facilities into risk rankings based on potential consequences, then the SVA seeks to determine the likelihood that the unwanted consequences can be prevented based on the security posture of the facility. Once facilities have submitted their SVA data, DHS will issue final tier rankings. Facilities that remain in one of the four tiers will be deemed “covered facilities” and, therefore, subject to CFATS regulations.
Step Three: Site-Security Plan (SSP)
The site-security plan ensures that covered facilities develop and implement a security plan appropriate for their relative risk. Each tier ranking has differing levels of performance required by their SSP.
The plan must respond to the specific issues raised by DHS in its final tier letter sent to covered facilities. The guide for developing the SSP is covered in a document called the "Risk Based Performance Standards" (RBPS). The RBPS is intended to provide the facility with flexibility in developing their SSP. Site-security plans will need to address 18 different parameters identified in the Risk-Based Performance Standards, including restrict area perimeter, secure site assets, screen and control access, theft and diversion, cyber, response, monitoring, training and personnel security. Once the SSP is complete, the facility submits it to DHS for review and approval. DHS then issues an analysis of the SSP that identifies gaps to be corrected, or it issues approval.
Step Four: Implementation and Inspections
Once a facility’s site security plan has been approved, the facility will have a limited time to implement its plan. DHS then begins on-site inspection to verify that the plan, as documented in the SSP, has actually been implemented.
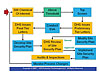
Figure 2.
Chemical-Terrorism Vulnerability Information (CVI)
During the course of implementing CFATS regulations, certain information is created, compiled, handled and transmitted to DHS by regulated (covered) facilities. This information has been characterized as Sensitive but Unclassified (SBU) information by DHS and is known as Chemical-terrorism Vulnerability Information (CVI). Detailed requirements exist for the proper handling of this information to protect it from public disclosure under the Freedom of Information Act (FOIA). The requirements are very specific and help protect this sensitive information from disclosure to unauthorized persons. KCI Protection Technologies has developed a CVI Security GuideTMto assist facilities in complying with CVI requirements.How KCI Protection Technologies Can Help
KCI Protection Technologies (KCI-PT) professionals were involved in some of the earliest risk assessment activities for chemical and other infrastructure sectors. With experience pre-dating 9/11 and the CFATS regulations, KCI-PT staff know the CFATS regulatory requirements, having supported some of the earliest preliminary research conducted by DHS and others.KCI-PT’s multi-discipline experience in chemical-process safety programs, fire-protection engineering, industrial security, life safety, security vulnerability assessments, risk management and process development enables it to provide engineering, consultation, and analysis services to Tier 1-4 facilities throughout the CFATS compliance process. KCI-PT provides assistance with security-vulnerability assessments, site-security plans, alternative-security plans, compliance audits, training, CVI education, awareness and self-inspection, and provides a practical CVI Security GuideTMto assist users with compliance to CVI guidelines.
For more information, phone (307) 479-7000 or visit www.kci-pt.com.